Advanced Encryption Standard (AES)
Contents
History
The history of the Advanced Encryption Standard started in 1997, when the National Institute of Standards and Technology (NIST) established a competition that aimed to pick a new cryptographic standard as an alternative to the Data Encryption Standard (DES) – the previous official Federal Information Processing Standard (FIPS) developed by IBM in 1977.
DES was internationally acclaimed and widely used standard that was implemented by governments and businesses but it became outdated and insecure due to its 56-bit key length. Key length (often referred to as key size) is the number of bits in a key that is used by a cipher. Small key size makes algorithm vulnerable to the attacks of the contemporary devices and the brute force computing solution method. Basically, it means that the cipher can be decrypted by the enumeration of all the possible solutions. In January 1999, distributed.net and the Electronic Frontier Foundation collaborated to publicly break a DES key in 22 hours and 15 minutes.
In addition to the mentioned vulnerability, DES was oriented on the hardware realization and software-based realization strongly lacked the efficiency.
On the January second, NIST announced its plans on the establishment of the replacement for DES. NIST decided to take the advices from the cryptographic community on how to choose the new algorithm. On the basis of the received feedback, NIST announced a competition and its requirements. New standard should’ve fulfilled the following principles:
- The competing algorithm should be a block cipher
- The block length of the cipher should be equal 128 bit
- It should support 128, 192 and 256 bit keys
A block cipher is a deterministic algorithm that operates on blocks – fixed-length groups of bits. Block ciphers are actively used to this day in the development of the cryptographic protocols. There were also several optional recommendations:
- The cipher should provide operations that are easily implemented both on hardware (in microchips) and on software (on personal computers and servers)
- The developers were encouraged to focus on 32-bit processors
- The structure of a cipher shouldn’t have been unnecessarily complicated so that all interested parties could be able to independently perform a cryptanalysis of the algorithm and ensure that it does not contain any undocumented features
Reasonably, the algorithms that aimed to become a standard must have been distributed freely, not exclusively and with no payments required for the patent usage. During the 9 months after the announce fifteen different cipher designs were created and submitted. They were tested by cryptographers on various architectures of PCs, were targeted with multiple types of attacks and had their speed and performance checked. Only 5 block ciphers managed to get to the final of the Advanced Encryption Standard competition. They were MARS, RC6, Rijndael, Serpent, and Twofish. They were analysed in the following, final round in which the Rijndael algorithm was chosen as a winner with a significant preeminence. It is the Rijndael algorithm, with several slight improvements, that is now referred to as the Advanced Encryption Standard and is one of the most popular encryption solutions in the world. It was announced as an upcoming governmental standard on November 26, 2001 and became effective on May 26, 2002. It is now encouraged to use by the National Security Agency (NSA) for top secret information encryption.
Description
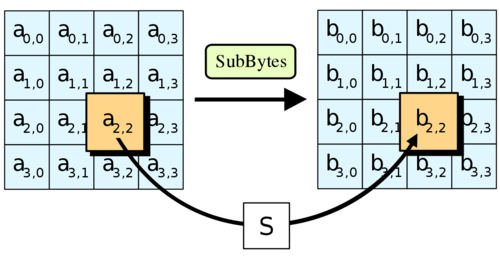
Advanced Encryption Standard (AES) is an encryption algorithm that managed to become on of the most used modern encryption and decryption methods. It is an upgraded version of the Rijndael algorithm – a block cipher developed by Vincent Rijmen and Joan Daemen. It uses one key to encrypt the data and the same key to decrypt it that makes it a symmetric-key algorithm.
Advanced Encryption Standard is designed in a way that makes it performance equally efficient both for hardware and software. Rijndael algorithm showed the best results in the hardware and software testing during the AES competition and this advantage was kept in the modern versions of Rijndael. The advantage in versatile computing efficiency was an outcome of the implementation of the block cipher design principle known as a substitution–permutation network.
Because the block size of 64 bits that was inherent to DES – an algorithm that was a standard before AES, turned out to be insecure due to the birthday paradox, Advanced Encryption Standard implemented a block size of 128 bits.
According to the birthday paradox, after a number of blocks becomes equal to the square root of the total number possible, there will be an approximately 50% chance of two or more blocks being the same which strongly simplifies the decryption and leads to the leaking of the information about the message contents. It means, that only 32 GB of data can be safely sent under one key while encrypted with the Data Encryption Standard. This amount of data was not a limitation the time of the IBM’s development of DES, but became strongly outdated in the nineties.
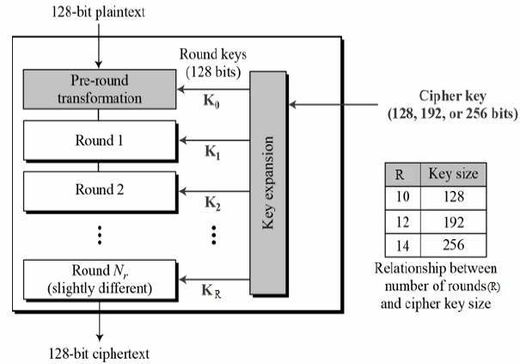
Because of mentioned problem, the participant of the Advanced Encryption Standard competition were required to support a block length of 128 bits that made it possible to send up to 256 exabytes of data without being afraid of the leakage of information. The original Rijndael algorithm supports block and key sizes of 128, 192 and 256 bits but in the AES version of Rijndael the block size is always 128 bits.
AES implementations
Advanced Encryption Standard is free-to-use for both commercial and non-commercial usage. As a winner of AES competition and NSA-approved algorithm, AES is very popular and worldwide used in various applications, libraries and hardware.
Libraries
C/ASM
Most of libraries that are compatible with ASE are written for C and assembly languages. It is often implemented in the software libraries that provide the development of the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols. Famous examples of this libraries are:
- GnuTLS
- OpenSSL
- LibreSSL
- mbed TLS
- wolfSSL
All these libraries are open-source implementations of TLS, SSL and DTLS (Datagram Transport Layer Security) protocols, that use AES as one of the options for the electronic data encryption. It is also widely used in libraries that are designed specifically for the data encryption. For example, it is applied in such solutions like:
- Libgcrypt
- LibTomCrypt
And AES-specific cryptographic implementations like, for example:
- AES Dust
- AES-256
- Open AES
C++ libraries
AES is a part of popular C++-based cryptographic library Botan, which is recommended for applications with increased security requirements by German Federal Office for Information Security. Another Advanced Encryption Standard implementation in the C++ libraries is Crypto++ – a software solution for the usage of cryptographic algorithms and schemes that was written by Wei Dai – a developer of “b-money” – a predecessor of bitcoin.
.NET
Microsoft’s software framework .NET Framework contains a full implementation of AES and a specialized version of it used in Microsoft’s Cryptographic Application Programming Interface (CAPI)
C# and Java
- Bouncy Castle Crypto Library is a group of cryptography-focused APIs for C# and Java that implements Advanced Encryption Standard
- Java Cryptography Extension is a standard Java extension that also offers AES for encryption
- Austrian Institute for Applied Information Processing and Communications (IAIK) has its own Java Cryptography Extension (JCE) that provides AES functional
Python
Advanced Encryption Standard is supported by several Python cryptography-focused libraries, some of which are:
- PyCrypto cryptography toolkit
- keyczar toolkit
- M2Crypto OpenSSL wrapper
- Cryptography library for Python
- PyNaCl binding for libSodium
JavaScript
Cryptography libraries differ in the implementations the number of supported AES modes. AES and other block cipher’s modes of operation are the algorithms that use a block cipher to provide an information service that the cipher is intended to. When the algorithm of block cipher only describes an encryption of one block of information, a mode of operation describes how to apply a cipher’s single-block operation to repeatedly transform the data larger than a block.
The US National Institute of Standards and Technology recommends 5 modes of block cipher operation. They are Electronic Codebook (ECB), Cipher Block Chaining (CBC), Cipher Feedback (CFB), Output Feedback (OFB), and Counter (CTR).
The following libraries support some of the modes but mostly not all of them and can expand their functionality, so they better be checked before the usage for the development.
- SJCL library
- AES-JS
- Forge
- asmCrypto
- pidCrypt
Applications
- The Advanced Encryption Algorithm is used in almost every archiver application. Most used examples are WinZip, Rar, 7z and UltraISO.
- It is used in such file encryption applications like Ncrypt and Gpg4win as well as in encrypting file systems like Microsoft’s NTFS and Linux’s F2FS.
- Disk and partition encryption solutions like VeraCrypt and Private Disk also often implement AES. Enterprisal encryption services like FileVault disk encryption solution of Mac OS X and Windows’ BitLocker support AES as well.
- Media access control (MAC) and physical layer (PHY) standards for wireless local area network (WLAN) communication use AES for the protection of the information that is spread in the network.
- The Advanced Encryption Algorithm is also often used in password management applications, online messengers and usb storage devices.
Hardware
- The Advanced Encryption Algorithm is implemented in Intel and AMD, as well as on SPARC S3 core processors.
- IBM mainframes of zSeries implement AES as the KM series of assembler opcodes when various Message Security Assist facilities are installed.
AES vs DES
| AES | DES | |
|---|---|---|
| Developer | Vincent Rijmen, Joan Daemen | IBM |
| Year of publishing | 1998 | 1975 |
| Derived from | Square | Lucifer |
| Key size | 128, 192 or 256 bits | 56 bits |
| Block size | 128 bits | 64 bits |
| Design structure | Substitution–permutation network | Feistel network |
| Rounds | 10, 12 or 14 depending on the key size | 16 |
| Known practical attacks | No | Brute Force Attack |
| Known theoretical vulnerabilities | Related-key attack, Known-key distinguishing attack, Key-recovery attack |
Differential cryptanalysis, Linear cryptanalysis, Davies Attack |
See Also on BitcoinWiki
Resources
- Wikipedia: Advanced Encryption Standard
- Wikipedia: List of cryptographic file systems
- Committee on National Security Systems: CNSS Policy No. 15, FS-1
- Alex Biryukov et al.: Key Recovery Attacks of Practical Complexity on AES Variants With Up To 10 Rounds
- Joan Daemen, Vincent Rijmen: AES Proposal: Rijndael
- The Twofish Team’s Final Comments on AES Selection
- James Nechvatal et al.: NIST’s Report on the Development of the Advanced Encryption Standard (AES)
- thebestvpn.com: Advanced Encryption Standard (AES)
- Wikipedia: Data Encryption Standard
- NIST: Reports on Information Security Technology
- CryptoAcademy: AES vulnerabilities
- CryptoAcademy: DES vulnerabilities














 Twitter
Twitter
 Telegram
Telegram
